Growth of the Cyber Insurance Market:
In the changing world of modern business, an unparalleled dependence on data and technology has led to new levels of cyber threats. In the face of this digital landscape, businesses today have no choice but to grapple with such cybersecurity necessities as strong protection against harmful online threats.
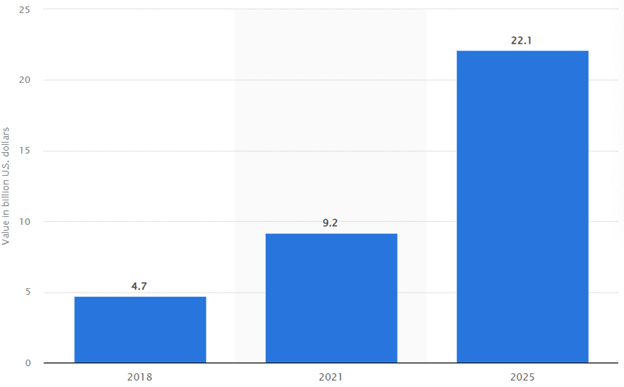
It is projected that the cyber insurance market will grow rapidly, more than doubling in size by 2025 and reaching around$22 billion. This astronomical growth highlights the increasing awareness regarding cyber insurance as an essential safeguard, aimed at protecting businesses from risks interwoven with data and technology’s widespread integration into their operations.
Source: Statista
In this regard, we will review the paramount value of cyber liability coverage in enhancing business and protecting them from financial hazards due to occurrences related to cyberspace.
The Current Situation for Cyber Threats
The latest data on cybersecurity technologies CAGR of 10.56% in 2024 reflects a significant transformation that can be observed within the industry nowadays.
This increase is far beyond the original estimates of growing 6.56% in 2022. These new predictions for year-on-year growth rate cannot be seen as anything but an indication that cyber threats are escalating with more vigor following introduction of Artificial Intelligence into cyberwarfare.
Automotive Hacking on the Rise
As the wave of automated vehicles spreads, a new frontier for cybersecurity challenges arises. Any modern car fitted with high level technology to enable functions such as cruise control and engine timing systems or driver assistance software that includes Bluetooth and WiFi technologies is vulnerable.
This translates to a 2024 sprouting automotive hacking threat that could result in taking control of the vehicle or eavesdropping through built-in microphones. With the emergence of autonomous vehicles, even more complexity is involved, necessitating strong cyber security to prevent any vulnerabilities.
For its part, vehicles are beginning to get connected with the internet. Therefore, the vehicle industry is exposed to increasing threats from cybersecurity attacks. Security measures that should be considered for connected vehicles are encryption, authentication and real-time monitoring. The automotive industry should focus on digital transformation, moving towards advanced hardware and software development to protect against possible data breaches.
Utilizing Artificial Intelligence Power
The combination of AI and machine learning has brought revolutionary changes in cybersecurity. These technologies are driven by AI that is used in the form of developing automated security systems, natural language processing, face detection as well threat detection.
Despite the fact that AI makes our prediction and defense of new attacks easier, it also creates difficulties as smart malware designed to circumvent current security protocols arises. The fair use of AI in cybersecurity becomes increasingly important as it grows and develops.
By transforming the cybersecurity industry, artificial intelligence has great potential. Automating security tasks, real-time detection and response to cyber threats is made possible via the use of AI-driven technologies. But organizations need to develop robust cybersecurity mechanisms to reduce AI related risks and prevent misuses of this revolutionary technology.
Mobile Devices as Prime Targets
Mobile devices are big targets for cybercriminals because we use them for many things. Mobile banking is coming under increasing attack. It is paramount to guard our smartphones against viruses and malware in 2024 due to the volume of private financial information they contain.
Cloud Security Challenges
Cloud computing is helpful for organizations, giving them flexibility and scalability. But it brings new security challenges because the cloud environment keeps changing.
Even though big companies like Google and Microsoft make cloud security strong, users need to watch out for problems on their end like viruses and phishing attacks. Keeping an eye on and updating cloud security measures is crucial to protect stored data.
Targeted Ransomware as a Pervasive Threat
One example of a targeted ransomeware attack is the WannaCry attack on hospitals in England and Scotland. Improved data security is necessary for companies facing the growing expansion of ransomware. As ransomware gets more advanced, organizations need better cybersecurity. They have to be ready for targeted attacks and use strategies to help stop them from causing major problems.
The rise in complex ransomware variants underscores the urgency for strengthened cybersecurity. As industries become more integrated, organizations need to strengthen their resistance against targeted ransomware and employ a proactive strategy that could prevent the disasters triggered by such campaigns.
Major Types of Cyber Liabilities and Coverage
As businesses face a much wider range of cyber liabilities today, it necessitates tailored coverage to mitigate potential financial and reputational losses. Here, we look into key types of cyber liabilities and how cyber liability coverage can serve as a critical shield against these risks.
1. Data Breaches and Cyber Liability Coverage
All businesses in every sector are battling against data breach risks. Robust coverage is imperative to understand the complex aftermath of such incidents.
- Privacy Liability: This facet of cyber liability coverage acts as a shield against legal repercussions stemming from unauthorized access, disclosure, or theft of sensitive data. It includes costs of defense, settlements and judgments post-data breach.
- Data Breach Response: Comprehensive coverage extends to the proactive management of data breaches. Addressing expenses related to notifying affected parties, providing credit monitoring services, and orchestrating public relations strategies, this component offers a reliable and coordinated response.
2. Cyber Liability Coverage Can Include Protection Against Social Engineering and Phishing Attacks
Businesses need to strengthen their defenses through specific cyber liability insurance that targets risks such as social engineering and phishing attacks. Funds transfer fraud is one example of this coverage.
- Funds Transfer Fraud: This coverage addresses the financial fallout resulting from unauthorized fund transfers due to social engineering or phishing attacks, providing financial reimbursement and support.
3. System Failure and Outages and Cyber Liability Coverage
Given systems’ vulnerability to failures and outages, organizations need cyber liability coverage beyond data breaches to cover wider problems with technology.
- Business Interruption: In the event of system failures or outages, this coverage compensates for lost income during the resulting downtime, providing financial support for the business.
- Extra Expenses: This facet of cyber liability coverage covers additional costs incurred to restore normal business operations, offering financial relief in the face of unexpected technological challenges.
But, as the virtual world develops so does cybercrime. Increasing the resilience of enterprises and limiting possible exposures through comprehensive cyber liability insurance is critical.
There for You: Acadia Insurance
At Acadia, we’re all about helping businesses throughout the Northeast thrive. Our mission is to provide superior service and product as close to you as possible, providing you with the coverage you need to proceed with confidence. We are committed to proactive risk management and comprehensive financial protection.
We understand what you want most from your insurance is security and peace of mind. That means knowing you are working with an insurance provider who will support you every step of the way to help you protect your business.
With Acadia, not only can you get coverage tailored to your needs, but you will also receive support from dedicated claims professionals to guide you through the claim process in the event of a loss. That way, you know exactly what to expect. Knowing your claims professional by name and a handshake – that’s “Closer Coverage”. Get to know more about how we work and find an agent near you by going to the Find an Agent section on our public website (www.acadiainsurance.com).
Acadia is pleased to share this material for the benefit of its customers. Please note, however, that nothing herein should be construed as either legal advice or the provision of professional consulting services. This material is for informational purposes only, and while reasonable care has been utilized in compiling this information, no warranty or representation is made as to accuracy or completeness. Recipients of this material must utilize their own judgment in implementing sound risk management practices and procedures.




